-

Open-Source Hearing Aids: A Look into the Future of Medical Technology and Coding
By Brooke Struyk Edited by Nataliya Brantly Abstract: Hearing loss affects a large portion of the global population, yet the prices for hearings aids continue to increase. With quality devices costing an upwards of $2000 per pair, and lasting between three to seven years depending on the model, access to these technologies has become…
-

Implementing AI in Music Recommenders and ethical concerns
By Kat Patten Abstract In 2022, the widespread use of generative AI has increased and since then it has been incorporated into our everyday lives. Not only can AI be used to look up simple questions, but it can be used to aid specific areas such as questions within a company, exercise tips, and…
-

Debunking Online Hitmen
Zoe Hess and Palen Kelly This paper will investigate the dark web, specifically the Onion Router (Tor) to explore what posts and websites relate to hiring a hitman. Is there a market related to contracting killing or violence? And is it easily assessable? While seemingly present in modern media through movies and tv series,…
-

How Does Political Repression in Iran Drive Dark Web Activity?
By Sutton Marks and Yancey Wegner Introduction On the topic human rights there have been numerous political protests in the country of Iran. Such protests have led to civil unrest and loss of lives, examples including Bloody November and the death of Mahsa (Jini) Amini in police custody. While citizens attempt justice against their…
-

Enhancing Cyber Threat Intelligence through Retrieval-Augmented Generation (RAG) Using a Knowledge-Aware AI Framework
By Muhammad Saiful Alam Introduction The increasing complexity of cyberattacks demands advanced tools capable of understanding and reasoning with evolving security information. Traditional detection systems utilizing static rule sets or signature-based methods often lag behind in adapting to the rapidly evolving tactics used by modern attackers. The latest development of Large Language Models (LLMs)…
-
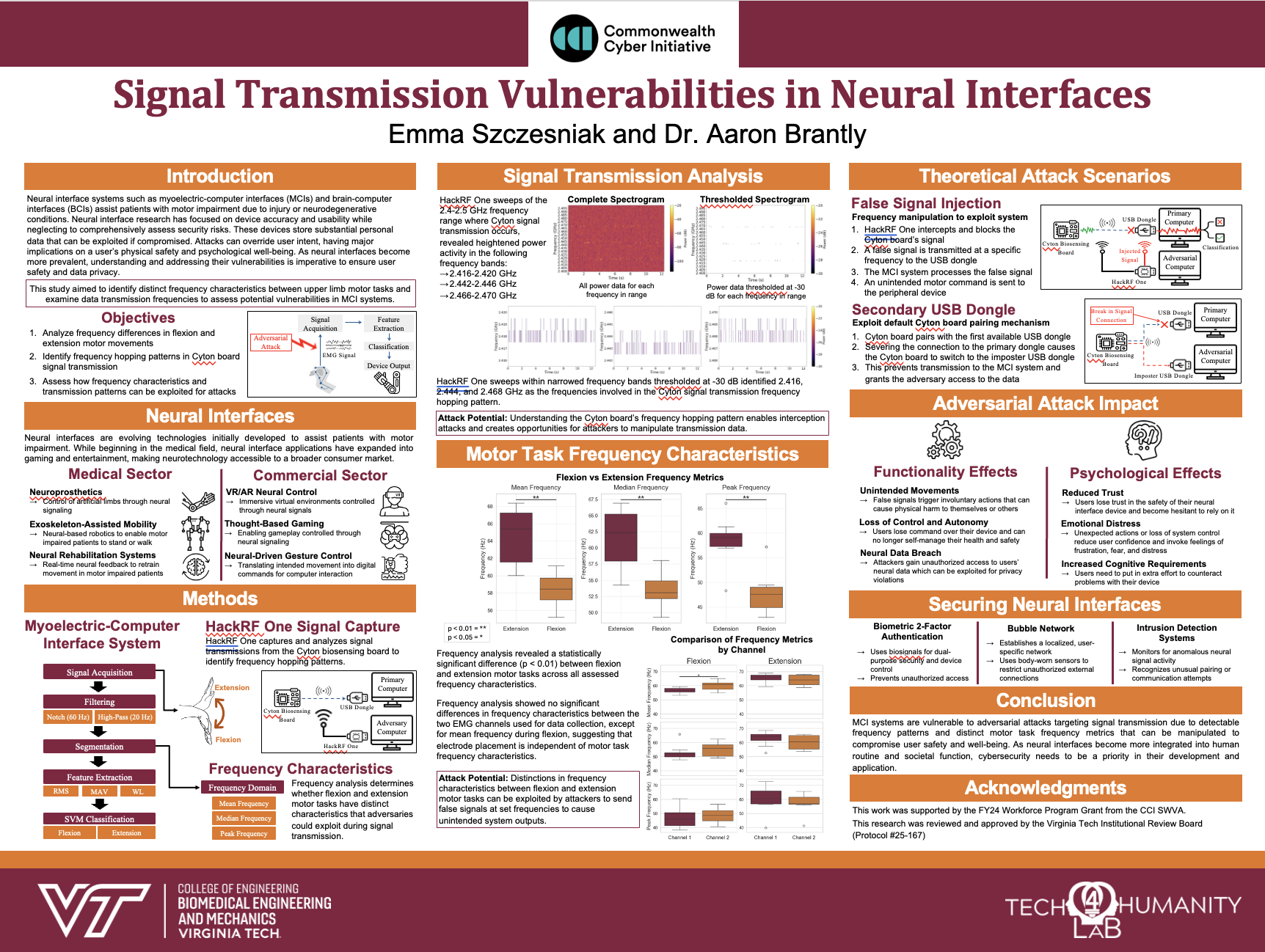
Signal Transmission Vulnerabilities in Neural Interfaces
by Emma Szczesniak Neural interface systems such as myoelectric-computer interfaces (MCIs) and brain-computer interfaces (BCIs) assist patients with motor impairment due to injury or neurodegenerative conditions. Neural interface research has focused on device accuracy and usability while neglecting to comprehensively assess security risks. These devices store substantial personal data that can be exploited if compromised. Attacks…
-

Changing Trends in U.S. Digital Health Security
By Dr. Nataliya D. Brantly U.S. healthcare has changed significantly since the early 2000s. This change was spurred by a number of studies that documented and exposed systemic failures, inefficiencies, poor coordination, and inadequate patient-centered care.[1]High levels of medical errors in a clinical setting, contributing to the thousands of deaths annually, emphasized the need to…
-
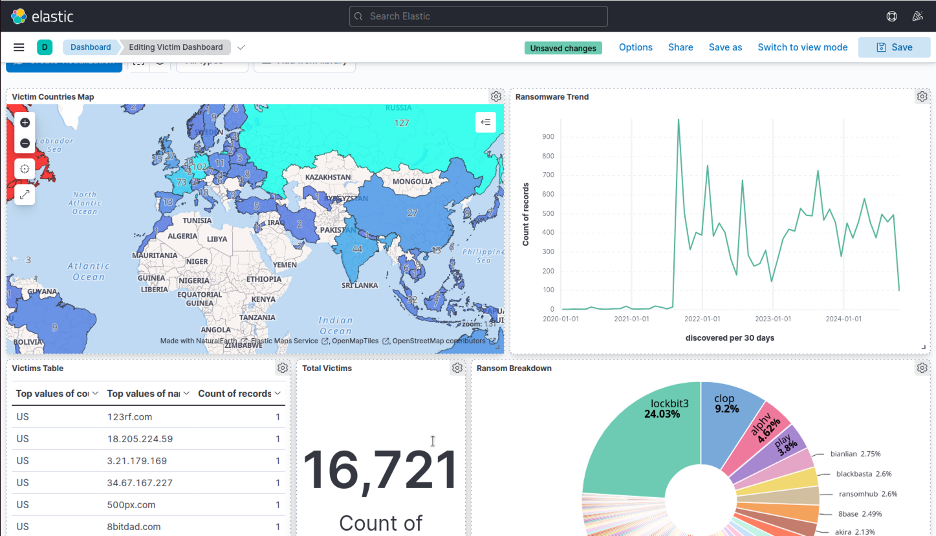
Visualizing Ransomware Data Available in Open Source Repositories
Ransomware poses a persistent threat in the cyber landscape. Over the past four years, there have been more than 19,000 recorded ransomware attacks and leaks, with the number of victims increasing daily. The massive number of attacks in such a short timespan highlights the importance of understanding the tactics employed by ransomware groups.
-

Ransomware and its Effect on Educational Institutions
Haleigh Horan and Divine Tsasa Nzita Ransomware attacks have become more common over the past several years and there has been a prominent spike in ransomware attacks against the education sector. As schools and school districts increase their use of technology across their enterprise operations they are increasingly viewed as potential targets with critical…
-
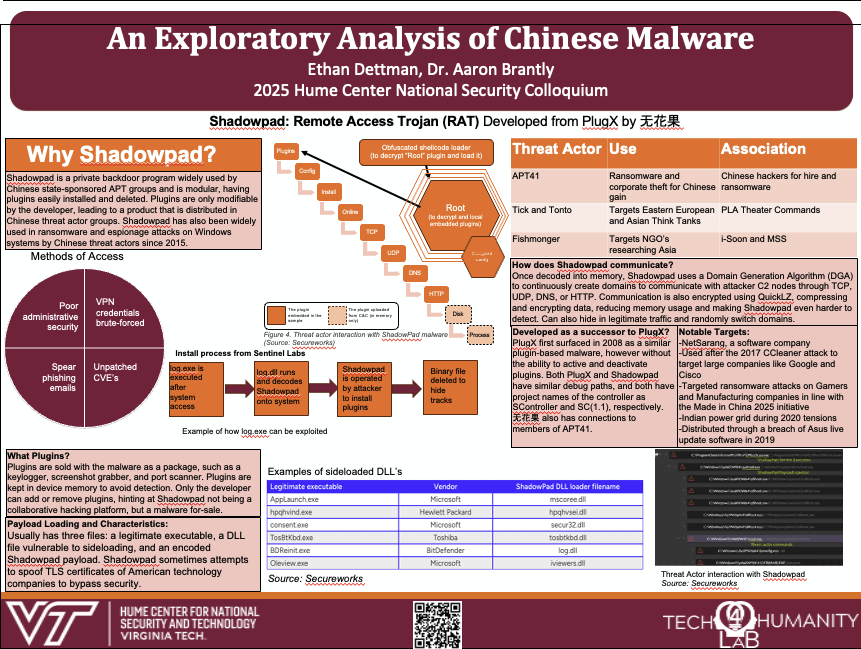
An Exploratory Analysis of Chinese Malware
By Ethan Dettman As cyber threats become more and more prevalent today, Chinese threat actor groups employ many malware packages to obtain information, both for personal gain and the benefit of the Chinese state. One of the most prevalent packages is Shadowpad, which has been used since 2017. Shadowpad is privately shared among Chinese-linked…
