-

Cybersecurity for Academics and Students
Join the Tech for Humanity Lab for a virtual workshop on how to protect your digital life, safeguard your research, and build responsible digital habits. When: November 17th, 2025 From: 10:30am – 12:00pm Where: https://virginiatech.zoom.us/j/88187329475 Event Overview This event seeks to empower students, faculty, and researchers with the knowledge and tools they need to…
-

Enhancing Cyber Threat Intelligence through Retrieval-Augmented Generation (RAG) Using a Knowledge-Aware AI Framework
By Muhammad Saiful Alam Introduction The increasing complexity of cyberattacks demands advanced tools capable of understanding and reasoning with evolving security information. Traditional detection systems utilizing static rule sets or signature-based methods often lag behind in adapting to the rapidly evolving tactics used by modern attackers. The latest development of Large Language Models (LLMs)…
-

Addressing Bias in AI Healthcare: Protecting Vulnerable Patient Populations
by Javaid Sofi Abstract AI’s integration into healthcare, while promising enhanced diagnostics and efficiency, carries a significant risk of amplifying health disparities affecting vulnerable populations. Bias arises from unrepresentative datasets (e.g., dermatology algorithms trained on lighter skin tones), cognitive biases in clinical labelling, and flawed proxies like zip codes conflating geography with health risk. Studies…
-
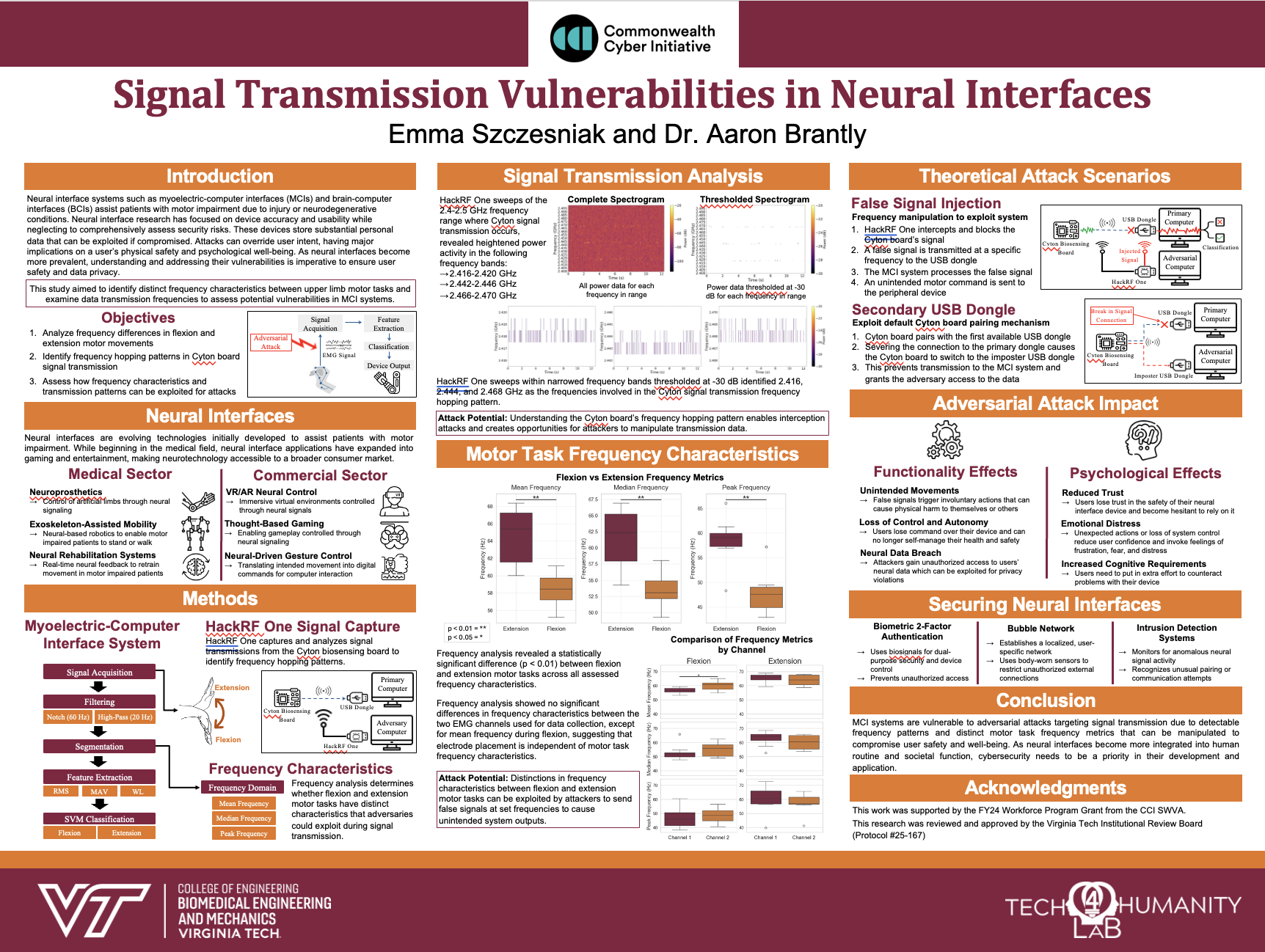
Signal Transmission Vulnerabilities in Neural Interfaces
by Emma Szczesniak Neural interface systems such as myoelectric-computer interfaces (MCIs) and brain-computer interfaces (BCIs) assist patients with motor impairment due to injury or neurodegenerative conditions. Neural interface research has focused on device accuracy and usability while neglecting to comprehensively assess security risks. These devices store substantial personal data that can be exploited if compromised. Attacks…
-

Generative AI Will Fail to Attract Us Because It Ignores What Makes Us Human
By Selim Tlili Selim Tlili has taught high school biology, chemistry and math since 2004. He began in the NYC public school system and moved to independent education in 2015. He is working on his first book in science education and is finishing his first movie. Read his work at selim.digital. I had an incredibly interesting lunchtime conversation…
-

Changing Trends in U.S. Digital Health Security
By Dr. Nataliya D. Brantly U.S. healthcare has changed significantly since the early 2000s. This change was spurred by a number of studies that documented and exposed systemic failures, inefficiencies, poor coordination, and inadequate patient-centered care.[1]High levels of medical errors in a clinical setting, contributing to the thousands of deaths annually, emphasized the need to…
-
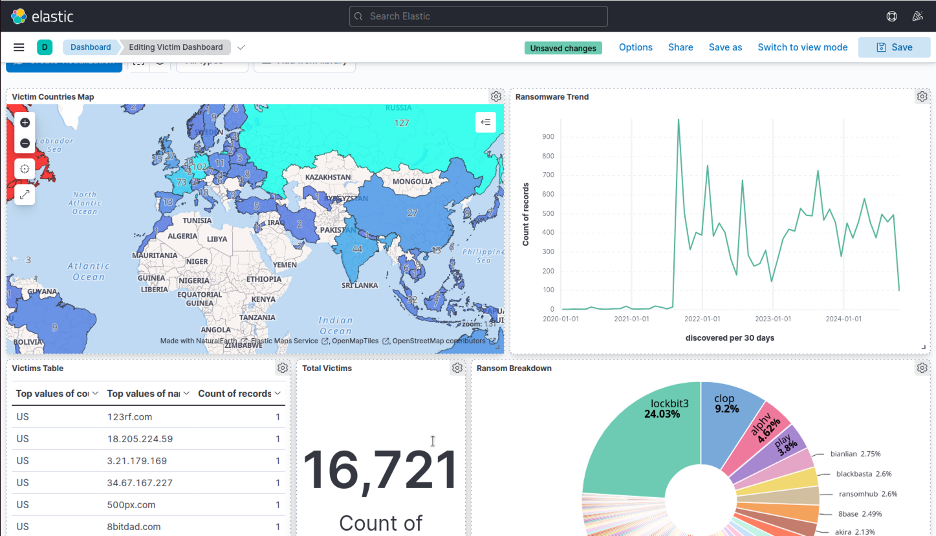
Visualizing Ransomware Data Available in Open Source Repositories
Ransomware poses a persistent threat in the cyber landscape. Over the past four years, there have been more than 19,000 recorded ransomware attacks and leaks, with the number of victims increasing daily. The massive number of attacks in such a short timespan highlights the importance of understanding the tactics employed by ransomware groups.
-

Ransomware and its Effect on Educational Institutions
Haleigh Horan and Divine Tsasa Nzita Ransomware attacks have become more common over the past several years and there has been a prominent spike in ransomware attacks against the education sector. As schools and school districts increase their use of technology across their enterprise operations they are increasingly viewed as potential targets with critical…
-
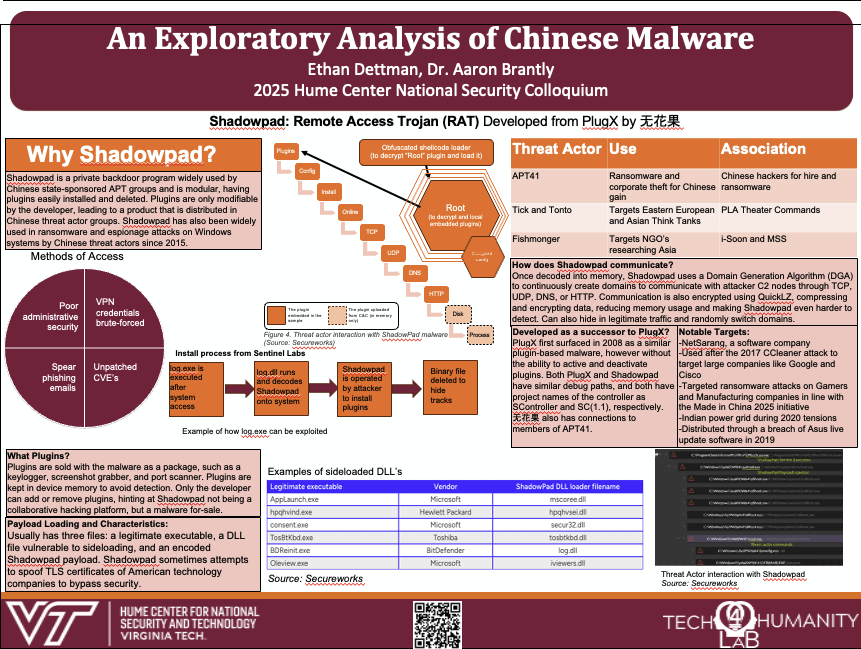
An Exploratory Analysis of Chinese Malware
By Ethan Dettman As cyber threats become more and more prevalent today, Chinese threat actor groups employ many malware packages to obtain information, both for personal gain and the benefit of the Chinese state. One of the most prevalent packages is Shadowpad, which has been used since 2017. Shadowpad is privately shared among Chinese-linked…
-

Developing a Spectrum of Gendered Surveillance-Facilitated Targeting
By Brooke Spens Abstract/Introduction In the modern era, surveillance practices have been used for various purposes from tracking a significant other to monitoring individuals’ data to generate profit. Through extensive research efforts, patterns surrounding the utilization of intrusive surveillance tools and instances of co-opting technology by those with malicious intent have emerged; the disproportionate…
