-

Developing a Spectrum of Gendered Surveillance-Facilitated Targeting
By Brooke Spens Abstract/Introduction In the modern era, surveillance practices have been used for various purposes from tracking a significant other to monitoring individuals’ data to generate profit. Through extensive research efforts, patterns surrounding the utilization of intrusive surveillance tools and instances of co-opting technology by those with malicious intent have emerged; the disproportionate…
-
VULNERABILITIES IN BLUETOOTH LOW ENERGY AND HOW THEY CAN BE LEVERAGED TO CAUSE HARM
By Christian Calvo Abstract Bluetooth Low Energy (BLE) is a wireless communication protocol designed for use in a variety of commercial devices. Devices that utilize BLE often have inferior security systems compared to alternative wireless devices, enabling malicious parties to more effectively execute adversarial attacks. To iterate the impact of adversarial attacks on BLE…
-

The Role of Honey Pots in Cyber Defense: An Introduction
Deception technology in the cybersecurity and ransomware space has long been regarded as a method of threat actor data collection with strong potential. Some of this technology includes Honeypots, Honeyfiles, and Honeynets – faux systems, files, and networks meant to mimic an organization’s digital resources to further understand new attack vectors and threat actor…
-
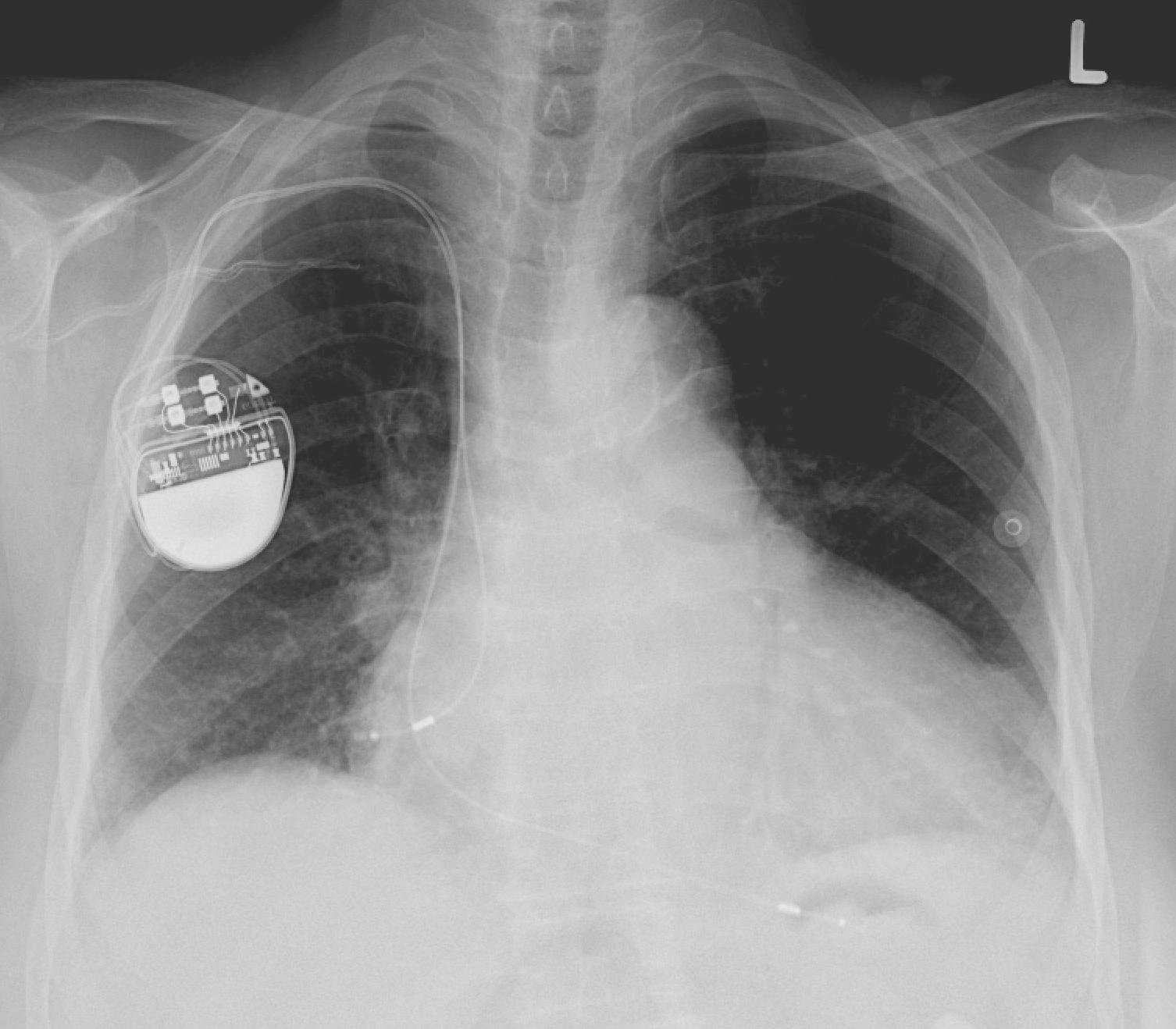
Regulating Custom Biomedical Devices: Challenges and Opportunities
The Food and Drug Administration (FDA) is a United States agency responsible for regulating medical devices among other functions. The regulation process entails a lengthy pre-market process that looks at pre-clinical trials, clinical trials, the warehouse in which the device is manufactured, ethics behind the device, and more. When it comes to the device…
-

AI’s Wetware Problem
When Project Mayhem won the DARPA Grand Challenge in 2014, the project lead from Carnegie Mellon, Dr. David Brumley, writing on his team’s success, quoted DARPA program director Mike Walker saying the program was just the ““beginning of a revolution” in software security.” What could be better than an AI white hat hacker finding…
-

LLMs – DeepSeek and Censorship.
The tech world has been rocked by the revelations of a more efficient and less expensive LLM created by the Chinese company DeepSeek. The revelations of the new model led to a single day $1 trillion loss on the U.S. Nasdaq 100. DeepSeek avoided U.S. microchip sanctions by training on the lower tier Nvidea…
-

Examining Pakistani Digital Surveillance and Privacy Rights
Pakistan presents a critical case study in digital surveillance and privacy rights within emerging democracies. An evolving framework of digital surveillance and censorship laws in Pakistan increasingly constrain personal rights to privacy and freedom of speech. Pakistan’s unique placement as a post-colonial emerging democracy offers a study of how emerging democracies adapt to the…
-

I am not a Luddite.
I am not a Luddite. Unlike English textile workers who fought the industrialization of manufacturing in the early 19th century, I generally embrace technology. In many ways, I consider myself to be a futurist and a leading-edge adopter of different forms of technology. I am a technically competent professor of political science; I have…
-

Reflections on the Student Conference on United States Affairs @ West Point (USMA)
In early October, I had the privilege of attending The Class of 1971 Student Conference on U.S. Affairs (SCUSA) at the United States Military Academy. This year marked the 75th anniversary of the conference since its inception in 1949. From the beginning, SCUSA has provided a unique opportunity for collaboration between more than 200…
-
A Brief Examination of LockBit
The Russia-affiliated ransomware group LockBit has become the most prolific ransomware of the modern day in part due to their Ransomware-as-a-Service (RaaS) model. Ransomware groups that use RaaS offer ransomware on dark web marketplaces to be used by attackers in exchange for some of the attackers’ profits.
